🚨 Crocodilus Banking Trojan: A New Android Threat

In March 2025, cybersecurity researchers from ThreatFabric sounded the alarm over a new Android threat: Crocodilus, a highly sophisticated banking trojan specifically targeting users in Spain and Turkey—but with the potential to go global.
Unlike typical malware clones, Crocodilus emerged as a fully-developed threat from day one, equipped with advanced capabilities like device takeover, credential theft, and black screen overlays, all powered by aggressive abuse of Android’s accessibility services.
🎯 How Does Crocodilus Spread?
Crocodilus is distributed outside of the Google Play Store, masquerading as legitimate apps like a fake version of Google Chrome (quizzical.washbowl.calamity). It reaches victims through:
- Malicious links shared via SMS, Telegram, WhatsApp
- Fake websites mimicking trusted brands
- Paid ads on social media platforms
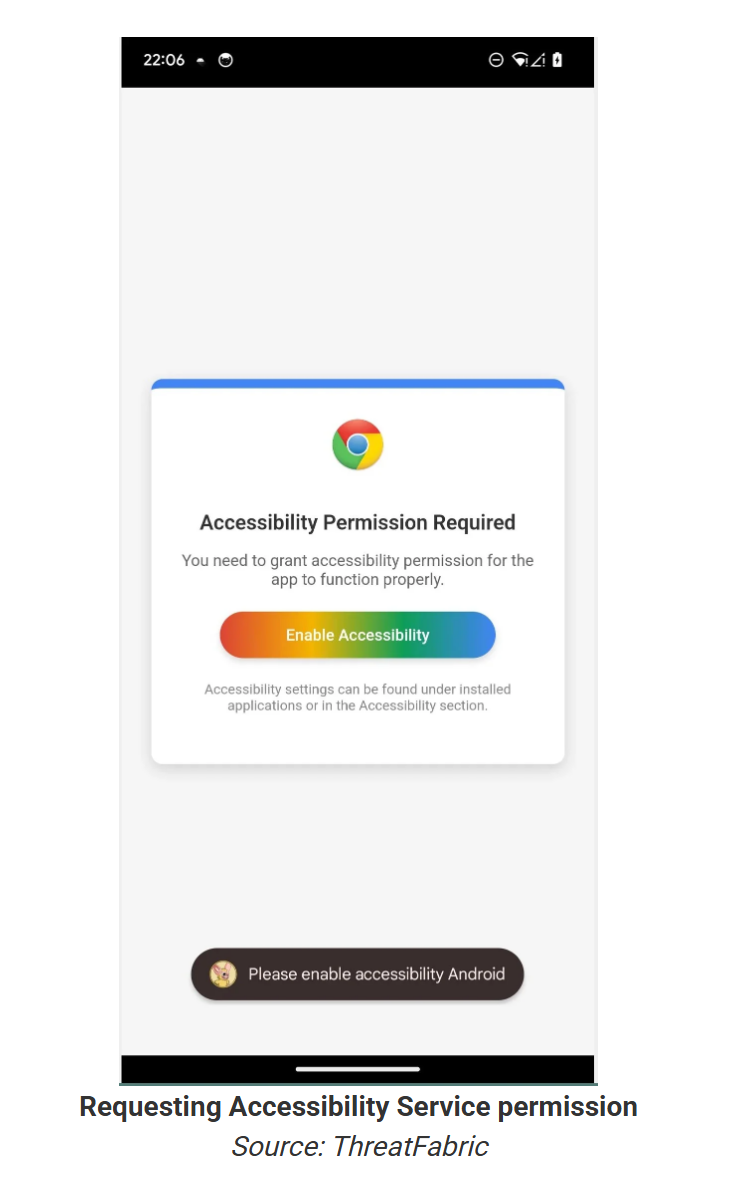
The APK acts as a dropper, engineered to bypass Android 13+ security restrictions. Once installed, it immediately prompts users to enable Accessibility Services—a critical step that unlocks full control over the device.
What Does It Do?
Once it obtains the necessary permissions, Crocodilus:
- Monitors launched apps – especially financial and crypto apps
- Uses overlays – fake login pages appear over real apps to steal credentials
- Captures screen content and accessibility events – it can see everything you see
- Targets Google Authenticator – capturing 2FA codes on-screen
Targeting Crypto Wallets with Deceptive Alerts
One of Crocodilus’ most deceptive features is an overlay pretending to be a warning: “Back up your seed phrase within 12 hours or lose your wallet!”
In reality, this is a clever trick to lure users into navigating to their recovery phrases, which are then silently harvested—granting attackers full access to wallets and assets.
Full Capabilities of Crocodilus
Crocodilus comes packed with a wide arsenal of features, including:
- Launching specific apps remotely
- Self-removal from the device
- Sending push notifications
- Sending SMS to selected/all contacts
- Harvesting contacts and installed apps
- Reading SMS messages
- Requesting Device Admin privileges
- Activating a full-screen black overlay
- Enabling/disabling sound and keylogging
- Setting itself as the default SMS manager
- Updating C2 server settings
“Crocodilus brings Device Takeover to a new level, using black screen overlays and remote control right out of the box,” ThreatFabric noted.
📉 Why Is It So Dangerous?
It runs silently in the background, maintaining persistence with clever techniques:
- Black screens to hide activity
- Muted audio to avoid suspicion
- Overlays that intercept inputs without raising alarms
Code analysis and debug messages suggest that the malware’s developer is Turkish-speaking, pointing to a regional operation with broader expansion potential.
🛡️ How to Protect Yourself
✅ Block installs from unknown sources – Only use apps from the Google Play Store.
✅ Be cautious of accessibility permission requests – Unless you're using apps built for accessibility purposes.
✅ Audit app permissions regularly – Revoke anything suspicious.
✅ Install a reputable mobile security app – Ideally one that can detect overlays and unusual background activity.
✅ Never type your crypto seed phrases into any app – Back them up securely offline and avoid prompts.
Final Thoughts
Crocodilus isn’t just another Android trojan—it’s a sign of how rapidly mobile malware is evolving. From banking app takeovers to seed phrase theft, it demonstrates a level of polish and maturity rarely seen in new threats.
As smartphones become the gateway to our entire digital lives, securing them is no longer optional—it’s essential.
🛡️ Concerned your phone may be compromised? Our mobile security assessments can uncover hidden threats before they cause damage.