MirrorFace Expands Cyber Espionage Operations: New Targets and Tools Unveiled
In a significant development, cybersecurity researchers have uncovered that MirrorFace, a threat actor group linked to China, has broadened its cyber espionage activities beyond its traditional focus on Japan. Recent findings indicate that the group targeted a diplomatic organization in the European Union, marking a notable shift in its operational scope.
Operation AkaiRyū: A New Campaign
Dubbed "Operation AkaiRyū" (Japanese for RedDragon), this campaign was detected by ESET researchers in late August 2024. The attack singled out a Central European diplomatic institute with lures related to the World Expo, scheduled to commence in Osaka, Japan, next month.
Evolving Malware Arsenal
Historically, MirrorFace has been known to deploy malware such as LODEINFO. However, in this operation, the group utilized a heavily customized variant of AsyncRAT and reintroduced ANEL (also known as UPPERCUT), a backdoor previously associated with APT10. The resurgence of ANEL is particularly noteworthy, as it had been discontinued around late 2018 or early 2019.
ESET's analysis suggests that MirrorFace has transitioned from using LODEINFO to ANEL, with no observed use of LODEINFO throughout 2024 and into 2025. This shift underscores the group's adaptability and evolving strategies.
Advanced Techniques and Stealth Measures
The intrusion also showcased the use of Visual Studio Code Remote Tunnels to establish covert access to compromised machines—a tactic increasingly favored by multiple Chinese hacking groups. The attack chains involved spear-phishing lures designed to persuade recipients into opening malicious documents or links. These would launch a loader component named ANELLDR via DLL side-loading, which then decrypts and loads ANEL. Additionally, a modular backdoor named HiddenFace (also known as NOOPDOOR), exclusively used by MirrorFace, was deployed.
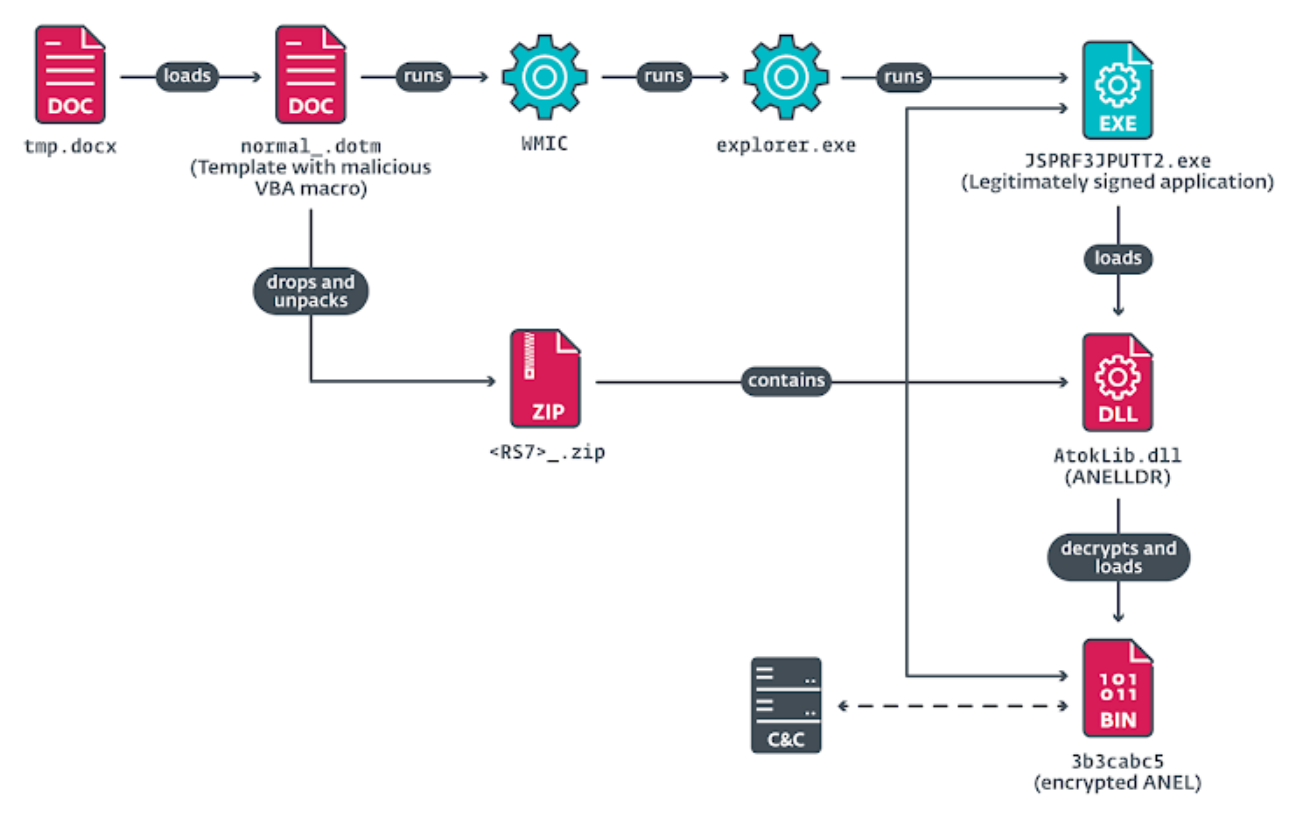
To hinder incident investigations, MirrorFace has improved its operational security by deleting delivered tools and files, clearing Windows event logs, and running malware in Windows Sandbox.
Implications and Recommendations
MirrorFace's expansion into European targets signifies a broader threat landscape and highlights the group's evolving tactics. Organizations, especially those in the diplomatic and governmental sectors, should remain vigilant and implement robust cybersecurity measures to defend against such sophisticated adversaries.
For a detailed analysis of Operation AkaiRyū and MirrorFace's tactics, techniques, and procedures, refer to ESET's comprehensive report.
Stay informed about the latest cybersecurity developments to safeguard your organization's digital assets.